Empowering Users and Institutions: A Risks and Opportunities Framework for Exploiting the Social Web
Empowering Users and Institutions: A Risks and Opportunities Framework for Exploiting the Social Web
Brian Kelly 1 Charles Oppenheim 2
1 UKOLN, University of Bath, Bath, UK
<B.Kelly@ukoln.ac.uk>
2 University of Loughborough, Loughborough, UK
<C.Oppenheim@lboro.ac.uk>
Abstract
Following the initial excitement generated by Web 2.0 we are now seeing Web 2.0 concepts being adopted across the cultural heritage sector. Libraries, with their responsibilities for facilitating access to information resources and engaging with their user communities, have been early adopters of Web 2.0, and the term 'Library 2.0' is now becoming accepted. Similar approaches are happening in the museums and archives sectors, with the terms 'Museum 2.0' and 'Archives 2.0' gaining currency.
But how should we ensure that the initial enthusiasms for use of Web 2.0 services and approaches become embedded within the organisation? And are cultural heritage organisations aware of the potential risks associated with making use of externally-provided services such as Facebook, YouTube and del.icio.us, including misuse of such services, associated legal concerns as well as the dangers of making use of services for which there may be no formal contractual agreements?
In this paper the authors argue that the cultural heritage sector needs to recognise that use of Web 2.0 providers does not necessarily provide an environment in which safe, secure and reliable delivery of services to the user community can be guaranteed. But rather than seeking to replicate successful Web 2.0 services in-house, we feel that we are in an environment in which cultural heritage organisations need to take a risk management approach to the use of networked services.
The paper describes a framework which is being developed which aims to ensure that institutions have considered the risks associated with use of Web 2.0 technologies and services and have identified strategies for dealing with potential risks in order to achieve the goal of balancing the risks and benefits in order to maximise the dividends to be gained by use of Web 2.0.
Keywords: Social Web, Web 2.0, risks
1 Introduction
The Web 2.0 term has now been widely accepted as a description of a new pattern of ways in which the Web is being used. The Web environment has progressed from the publishing paradigm which characterised what is now sometimes referred to as Web 1.0, in which small numbers of content creators use tools ranging from desktop HTML authoring tools though to enterprise Content Management Systems and corresponding editorial and quality assurance processes to produce content for passive consumption by end users.
In a Web 2.0 environment large numbers of users are creating content using an ever-increasing variety of tools with such content being made available via a wide variety of commercial Web 2.0 services including photographic sharing services such as Flickr, video sharing services such as YouTube and social networking services such as MySpace and Facebook.
The characteristics of Web 2.0 were described by O'Reilly [1]. The key areas relevant to this paper include: (a) application areas including blogs and wikis, social sharing services and social networking services; (b) the ease of reuse of content elsewhere through syndication technologies such as RSS; (c) a culture of openness and sharing, which has been helped through the development of copyright licences such as Creative Commons; and (d) the concept of the "network as the platform" by which services are hosted on externally-hosted services and accessible over the network, rather than a managed service within the organisation.
The Social Web is closely linked to Web 2.0. But whereas Web 2.0 includes various technical aspects (including technologies such as RSS and AJAX) the focus of the Social Web is very much focussed on the connections between people.
2. Opportunities
Why should cultural heritage organisations be interested in Web 2.0 and the Social Web? Answers to this question may include:
- The Social Web is popular.
- Social Web services can provide an opportunity to engage with new user communities and address challenges such as widening participation and social inclusion.
- Cultural heritage organisations, which are concerned with sharing and maximising access to cultural and scholarly resources, can exploit the Social Web to further this key mission.
- The Social Web can be cost-effective, allowing cultural heritage organisations to exploit a technical infrastructure that is already in place and is popular with many users.
- The economic downturn means funding for in-house development work is difficult to obtain.
- Popular Web 2.0 services can be easily used by end users as they can make use of services and interfaces they may already be familiar with.
These opportunities have been identified by many cultural heritage organisations which are already exploiting the Social Web’s potential. Some examples of how museums, libraries and galleries are exploiting the Social Web are given below:
The National Library of Wales (NLW) has a remit to collect, preserve and give access to all kinds and forms of recorded knowledge, especially relating to Wales and the other Celtic countries, for the benefit of the public, including those engaged in research and learning. The use of Web 2.0 approaches for Library 2.0 delivery is ingrained in the NLW's 2008 strategy document Shaping the Future [2] which outlines the Library's desire to explore collaborative and diverse models using external resources. This will allow the NLW to leverage Web platforms which are heavily focused on user engagement in order to deliver future services.
The Brighton on the Pull Project provided an opportunity for Brighton Museum & Art Gallery to work with target audiences and new ways of researching their collections. The ethos of On the Pull was concerned with taking a step away from the traditional museum exhibition to encourage new visitors and target audiences. The project team explored use of social networking services as a marketing tool in order to get away from the associations with the word ‘museum’ as a way of breaking down barriers and the connotations the word was found to hold for the focus groups. Music and video clips hosted on YouTube are embedded in MySpace. In addition to MySpace, FaceBook was also used as a marketing tool to advertise events, promote competitions, display promotional images, images of objects from the collections and play music [3].
The arrival of a pair of nesting peregrine falcons at Derby Cathedral provided Derby Museums with an opportunity to promote the town to a large audience. A Webcam provided live video footage of the nesting of three chicks and an accompanying blog and MySpace account, together with use of Flickr and YouTube for providing access to photographs and video footage resulted in “evidence emerging of visitors coming to Derby specifically because of its peregrines” [4].
3. Risks and Barriers
3.1 Identifying the Concerns
UKOLN, a national centre of expertise in digital information management based at the University of Bath has, over the past two years, delivered a series of workshops for the UK’s cultural heritage sector. The workshops have provided an opportunity for practitioners in the sector to gain an understanding of the potential of Web 2.0 and to explore its potential. The workshops have also identified barriers to the effective deployment and use of the Social Web. A summary of the various concerns is given below.
Sustainability Challenges: There may be concerns over the lack of interoperability of third party services, with dangers that a service may be a 'walled garden', allowing data and content to be added to the service or created within the service but cannot be exported to another environment.
Technical Challenges: IT support staff may raise technical concerns related to reliance on third party organisations to deliver services for the organisation. These concerns might include performance and reliability issues, security, backups, etc.
Interoperability Challenges: Technical concerns raised may also cover the interoperability of third party services with other systems. This might include integration with existing in-house services and the export and migration of data to other services, including replacement services which might not be currently available.
Support Issues: Although many popular Social Web services can be used without formal training or support, use of the services in an institutional context may generate user queries.
Individual Concerns: Individuals within the organisation may be concerned with the deployment of Social Web services. Staff within the organisation may be reluctant to use technologies such as blogs and micro-blogging services such as Twitter because of an unfamiliarity with the technologies or the culture and expectations in these technologies or a desire to keep professional and social activities separate.
Organisational Issues: Proposals to make use of Social Web services by a cultural heritage organisation may not be universally welcomed by everyone within the institution. This may be regarded as undermining the organisation or a department in the organisation. Such concerns may not be openly articulated, but may lie behind concerns raised listed above.
3.2 The Legal and Related Concerns
There are a number of legal risks involved in creating and using resources hosted on Social Web services. Briefly, they can be summed up as follows:
- Putting materials in that one should not deposit, because the copyright or other Intellectual Property Rights are held by third parties.
- Use of Registered Trade Marks or unregistered trade names without permission.
- Failure to identify someone as an author when they should be so named – this may well be an infringement of their Moral Right of paternity.
- Failure to respect the Moral Rights of authors e.g. derogatory treatment of their work.
- Data or advice that is inaccurate or misleading, and could lead to financial, physical or other damage to third parties if followed.
- Outputs that break the Data Protection Act or infringe personal privacy.
- Outputs that contain illegal materials e.g. materials that are pornographic, encourage terrorism, are defamatory, are in Contempt of Court, break race or sex discrimination laws, etc.
- Outputs that break the Disability Discrimination Act by being unreadable to those with impairments.
4. A Risks and Opportunities Framework
4.1 The Tensions
This paper has provided examples of use of the Social Web by cultural heritage organisations which have identified the benefits which the Social Web can provide in enhancing the range and quality of services to the organisations’ user communities. However we have also listed a range of concerns which organisations considering making use of Social Web services will need to consider. We will now describe a risks and opportunities framework which has been developed in order to support cultural heritage organisations in making decisions on use of the Social Web.
4.2 A Risks and Opportunities Framework For Addressing The Tensions
A risks and opportunities framework has been developed to support cultural heritage organisations in making effective use of the Social Web [5]. This paper introduces further developments to the framework including a summary of risk minimisation approaches and an inclusion of an evidence base.
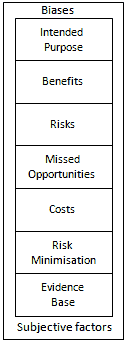 Use
of the framework involves documenting the following aspects of the
proposed use of the Social Web:
Use
of the framework involves documenting the following aspects of the
proposed use of the Social Web:
Intended use: Rather than talking about Social Web services in an abstract context (“shall we have a Facebook page” for example) specific details of the intended use should be provided.
Perceived benefits: A summary of the perceived benefits which use of the Social Web service are expected to provide should be documented.
Perceived risks: A summary of the perceived risks which use of the Social Web service may entail should be documented.
Missed opportunities: A summary of the missed opportunities and benefits which a failure to make use of the Social Web service should be documented.
Costs: A summary of the costs and other resource implications of use of the service should be documented.
Risk minimisation: Once the risks have been identified and discussed approaches to risk minimisation should be documented.
Evidence base: Evidence which back up the assertions made in use of the framework.
When using this framework it should be recognised that there are likely to be biases, prejudices, vested interests and other subjective factors which will affect how the framework is used. Ideally such subjective factors will be openly acknowledged and taken into account, although it is recognised that this may be difficult to achieve.
4.3 Application to In-House Developments and Existing Services
It should be noted that this framework need not only be applied to proposals to make use of the Social Web. In order to minimise the subjectivity of the approach it should also be applied to proposed in-house development work and commissioning IT developments. It can also be applied to existing services in order to identify the risks, limitations and constraints which the organisation is willing to tolerate and accept.
5. Legal Risks
5.1 A Risk Assessment Formula for Legal Infringements
The risks and opportunities framework recognises that although there will be risks when seeking to exploit the Social Web it may be necessary to accept such risks in order to deliver services to the user community. A similar approach can be taken to addressing the risks associated with possible copyright infringement.
The example below relates to copyright infringement, but the same formula applies to all the legal risks identified above. The risk can be calculated as follows:
R = A x B x C x D
where R is the financial risk; A is the chances that what has been done is infringement; B is the chances that the copyright owner becomes aware of such infringement; C is the chances that having become aware, the owner sues and D is the financial cost (damages, legal fees, opportunity costs in defending the action, plus loss of reputation) for such a legal action. Each one of these other than D ranges from 0 (no risk at all) to 1 (100% certain). D is potentially a high number. It is not easy to calculate the cost of loss of reputation.
Factors to bear in mind:
- If the work is to be used in a commercial context (i.e. to generate financial gain) then a rights owner who later becomes aware of the use of their work may be more likely to pursue an action for infringement of copyright than if the work is being purely used for educational purposes.
- The nature of the content used, for example, the rights in high value content, such as commercially produced films, text, images, music and software, are more likely to be actively enforced by their owners.
- Particularly sensitive subject areas are music, geographic data, literary works by eminent authors, and artistic works including photographs and drawings.
- Is there any track record of the contributor ignoring legal niceties in the past?
- Is there any track record of a particular third party having complained before?
Depending on these factors, the risks will vary. However, a Web 2.0 provider that ignored warning signals (e.g. a contributor who ignored legal niceties in the past is allowed to continue to add more materials without checks being made) is likely to receive an unsympathetic hearing from the Courts. Similarly, a service provider who has failed to educate contributors regarding legal issues will also not be viewed sympathetically by a Court.
Ultimately, it is important that the service provider is proportionate about possible risks whilst at the same time prepares suitable mitigating strategies in the eventuality of a complaint. An apology and promise of swift action to rectify is often sufficient.
5.2 Reducing the Legal Risks
A cultural heritage organisation making use of the Social Web should ensure that it has clear and robust notice and take down policies and procedures with a clear address given for complaints. The notice and take down policy adopted by JORUM would be a valuable starting point [6]. Clear instructions should be given as to where and to whom notification of allegedly illegal content should be sent, along with details of the complainer, the complainer's interest in the matter and where the complainer can be contacted. Processes should be put in to place to act expeditiously on such a notification.
6. Conclusions
We have seen how cultural heritage organisations are successfully exploiting the Social Web in order to deliver quality services to their user communities. There is, however, an awareness that there are a variety of risks associated with use of the Social Web. The use of a risks and opportunities framework and a risk assessment formula have been described which aim to support the discussions and policy-making processes organisations need to take when formulating policies on exploiting the Social Web.
References
- What Is Web 2.0? O’Reilly, T. Retrieved September 20th 2009: http://www.oreillynet.com/pub/a/oreilly/tim/news/2005/09/30/what-is-web-20.html
- Shaping the future: The Library's strategy 2008-2009 to 2010-2011, National Library of Wales. Retrieved September 20th 2009: http://www.llgc.org.uk/fileadmin/documents/pdf/Strategy2008-2011.pdf
- On The Pull, English, C. UKOLN Cultural Heritage blog, 2 April 2009. Retrieved September 20th 2009: http://blogs.ukoln.ac.uk/cultural-heritage/2009/04/02/the-on-the-pull-project/
- When Peregrines Come To Town, Moyes, N, UKOLN Cultural Heritage blog, 18 May 2009. Retrieved September 20th 2009: http://blogs.ukoln.ac.uk/cultural-heritage/2009/05/18/when-peregrines-come-to-town/
- Time To Stop Doing and Start Thinking: A Framework For Exploiting Web 2.0 Service, Kelly, B., Museums and the Web 2009 Conference. Retrieved September 20th 2009: http://www.ukoln.ac.uk/web-focus/papers/mw-2009/
- JORUM procedures to Deal with Queries, Alerts and Complaints, JORUM. Retrieved September 20th 2009: http://www.jorum.ac.uk/docs/pdf/takedown_procedure.pdf