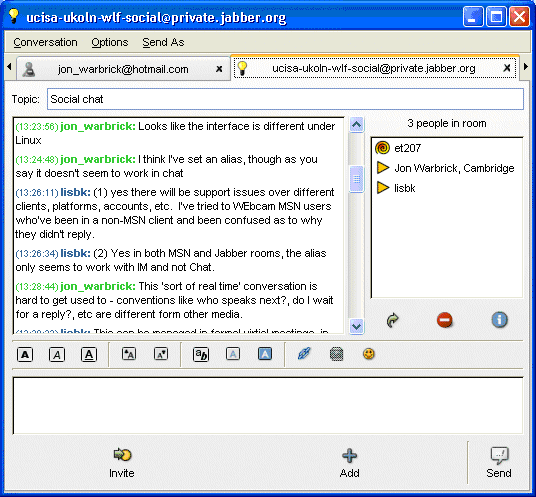
Figure 1: A Jabber Instant Messaging Chat
Brian Kelly*, Emma Tonkin* and Paul Shabajee+
* UKOLN, Bath, BA2 7AY, UK
{B.Kelly, E.Tonkin}@ukoln.ac.uk
+ ILRT, University of Bristol, BRISTOL, BS8 1HH
Paul.Shabajee@bristol.ac.uk
The increasing availability of WiFi networks in conference venues is an opportunity to provide additional services for conference delegates and to enhance and enrich the learning experience.
This paper reviews experiences of use of networked applications in a conference environment and outlines a number of potentially useful technologies. The paper addresses potential concerns over use of networked technologies including the dangers of disruption and distraction, legal and copyright issues as well as the danger of being over-fixated on the technologies themselves, rather than the uses they can provide.
The paper concludes by summarising the issues which need to be addressed when considering the provision of networked services in a conference setting.
Many international conferences, especially those in the IT sector, nowadays provide a WiFi network infrastructure - indeed, there is an increasing expectation, especially from seasoned conference delegates from North America, that WiFi networks will be provided as standard at international conferences.
Initially WiFi networks were used primarily by delegates to access their email. However we are now beginning to see innovation in the use of networked technologies to enhance the learning experiences and administrative support at conferences. Initiatives such as UKERNA's Location Independent Networking project [9], which seeks to facilitate "hassle free" network access for visitors to UK higher and further education institutions will help to encourage take-up of such technologies.
The use of networked technologies in a conference setting does raise a number of issues which will need to be addressed. For example, will use of networked devices be disruptive to other delegates; will broadcasting or recording of talks infringe copyright or inhibit discussions. In addition to these issues, if it is felt desirable to be proactive in providing access to networked applications, it will be necessary to choose the applications areas, recommend appropriate applications, devise an acceptable use policy, etc.
UKOLN, a national centre of expertise in digital information management based at the University of Bath, organises and participates in many national and international conferences, workshops and seminars. UKOLN has been developing links with UCISA (Universities and Colleges Information Systems Association) in order to identify possible areas of joint work. It was felt that a joint event on ways of exploiting collaborative applications would provide an appropriate topic, covering both UKOLN's involvement in such technologies and the need to understand the challenges facing the institutions which will provide the local infrastructure and be responsible for delivering the service.
This paper describes our experiences in participating at such events and the experiences we gained in organising a workshop which sought to exploit networked applications during the course of the event. We conclude by identifying some of the key issues which will need to be addressed by organisations wishing to take a similar approach.
For several years networked technologies have been used to support the Advisory Committee (AC) meetings of the World Wide Web Consortium (W3C). An IRC (Internet Relay Chat) service has been used to support minute-taking at the meetings. This is particularly useful at formal meetings of an international consortium, when highly technical and specialist topics will be discussed and when participants whose native tongue is not English are speaking. Formal transcripts of the IRC discussions are published allowing representatives to view the discussions subsequently. A W3C AC meeting was held in Budapest, Hungary in May, 2003, immediately prior to the international WWW 2003 conference. Since the WiFi networked provided for the AC meeting was still in place many of the delegates made use of the network during the conference. As described by Shabajee [6] IRC and the Web was used to enrich the conference by allowing, for example, researchers to engage in discussions during a conference presentation and provide well-formulated questions during the question time. Shabajee's article coined the expression "Real-time Peer Reviewing" to describe this phenomenon.
At the Colston Symposium held at the University of Bristol, UK in March 2004 Shabajee reviewed the approaches taken at the WWW 2003 conferences and described reactions of fellow participants [7]. At the symposium itself the event organisers provided a similar networked environment, with one new addition: the IRC dialogue was displayed live during the presentations, alongside the speakers slides. Feedback on the use of IRC, together with related software such as Blogs for notes of the talks and discussion group sessions, was obtained, which indicated mixed reactions.
At the UCISA Management Conference held in Manchester in March 2004 Kelly [2] argued that with the acceptance of instant messaging (and SMS texting) amongst young people and the take-up of mobile devices such as mobile phones, digital voice recorders, digital cameras, etc. we can expect to see students seeking to make use of such technologies during their courses. He also pointed out that collaborative technologies, such as instant messaging, Blogs, Wikis, etc. are likely to grow in popularity, especially to support teaching and learning - learning is, after all, very much a social activity. There is therefore a need to explore the potential and to put in place appropriate mechanisms which will ensure that the network is used to enhance the learning process and not distract from it. Kelly suggested that, as the conference venue actually provided WiFi access, it was unfortunate that its capabilities were not being exploited and that this should be addressed at future UCISA events.
The provision and support for networked applications in a conference or formal teaching context is likely to require the involvement of an institution's IT Services department. In order to engage the IT services community in discussions of the issues in providing a networked support to support the scenarios outlined above the author co-facilitated a day's workshop on this topic with UCISA - an organisation which represents the whole of higher education, and increasingly further education in the UK, in the provision and development of academic, management and administrative information systems. The event - Beyond Email - Strategies For Collaborative Working In The 21st Century - provided "an opportunity for delegates to gain an understanding of these technologies and hear about how they can be used ... [and] to address the challenges which need to be faced when deploying such tools in an institutional context" [10].
The availability of a WiFi network at the workshop venue enabled delegates to make use of networked applications at the event and not just listen to case studies and discuss their use. Shortly before the event the delegates were emailed announcing the availability of the network and were encouraged to install and try a number of applications in advance of the event, if they were intending to bring along a networked computer.
The applications which were to be used were a Jabber-based instant messaging client, such as GAIM and the Wikalong Firefox extension (although any Web browser could also be used). Further information on these applications was provided [11].
An example of use of the Jabber instant messaging software is shown in Figure 1.

Figure 1: A Jabber Instant Messaging Chat
During the workshop a number of virtual rooms were set up for use by the delegates and the Wikalong tool was available, primarily for use during the discussion group sessions to enable members of the discussion groups to collaborate in the notes for the reporting session. An example of the Wikalong interface is illustrated in Figure 2.
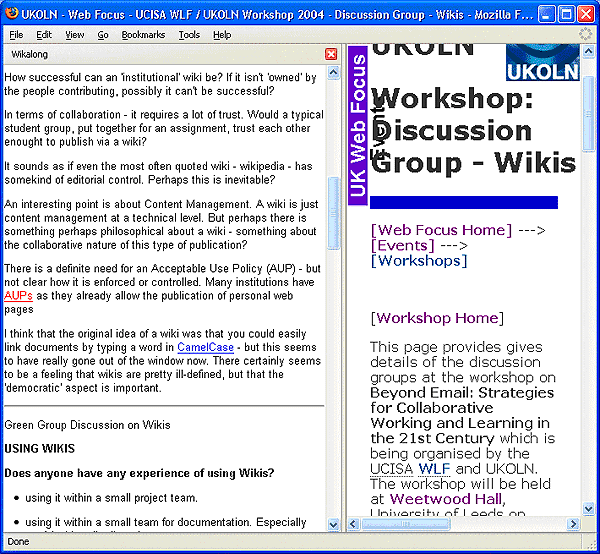
Figure 2: The Wikalong Annotation Software
In addition to the tools used by the delegates, the Skype Internet telephony application was also used to enable a remote participant to listen in to the initial presentation.
Experienced IT support staff will appreciate the need for an acceptable use policy (AUP) which covers acceptable and unacceptable use of IT services. The use of collaborative technologies and mobile devices may well require extensions to existing AUPs. An AUP covering use of such technologies and devices at a conference may be a need to address issues such as noise and disruption, copyright, etc.
An AUP was developed for the workshop which covered these issues [12]. In brief the AUP stated that use of networked applications and mobile devices were permitted in order to support the aims of the day, provided such use did not distract others, interfere with the running of the event or infringe others' privacy or copyright. The AUP provided examples of possible dangers such as:
Although over 40 of the 80+ workshop delegates had expressed interest in bringing along a networked computer, in practice only about 10-15 logged in during the day. This was partly due to difficulties experienced by some delegates in logging in but also perhaps a reluctance to experiment with new applications whilst at the same time learning new concepts. One delegate subsequently published on his Blog [5]:
"... on the day I was unable to get past the authentication screen; in fact it was left mainly to the Mac users to collaborate online as most others failed like myself to get past the first hurdle .... Anyway, perhaps it was better for me just to listen and tap as there was a lot to absorb - and herewith jottings relating to blogs."
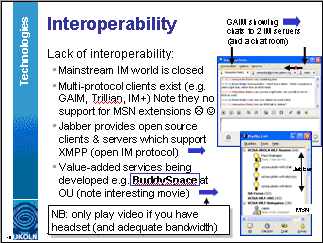
Figure 3: Design Of A PowerPoint Slide
Speakers at the workshop were asked to provide their slides prior to the event. The slides were then made available (in HTML and PowerPoint formats) from the workshop Web site, as a resource that could be accessed by delegates during and after the event. Speakers were encouraged to use their slides to provide links to resources, as illustrated in Figure 3 [3].
As shown, hyperlinked resources are clearly labelled. The links were designed to provide access to more detailed resources (effectively acting as a reading list) or to allow delegates to access resources on topics of particular interest to them (and thus providing additional learning routes to what would often be a one-dimensional presentation).
It should be noted that providing access to the slides also has accessibility benefits. In order to demonstrate this one slide contained text which was too small to read and delegates asked to discover what the text said (which could be done in several ways, including changing the style sheet of the HTML file, zooming in on the text or copying the text and pasting to a text editor). Although this exercise was planned to demonstrate the potential, it was found that delegates sitting at the back of the seminar room could not see text near the bottom of the screen. However those with networked access could see the slides on their own device!
Delegates who did make use of the technologies appeared to find their use valuable and could appreciate their potential. The use of a Wiki for note-taking of the discussion groups seemed to be particularly successful. For example, in response to the discussion group question "Should we be promoting/providing Wikis?" one group reported [13]:
"Yes. There could be real benefit and exciting possibilities in every area of institutional activities: teaching&learning, research, administration and user support. We need to get in there first and understand what users need and what they might do. We also need first make better use of wikis ourselves so we can full understand them and consider how we can then deploy them in an easy to use and manageable service."
In addition to the Wiki, a number of virtual discussion rooms were available prior to, during and for a short period after the workshop. The Jabber messaging environment [1] was used to create three of virtual discussion rooms which were intended to provide a environment for testing and social shat, for technical queries and to discuss the workshop content (although in practice, discussions were split across the three virtual discussion rooms and, on reflection, it might have been better to provide only a single room).
As can be seen from the transcript [14] there was a substantial amount of discussion in the ucisa-ukoln-wlf-social room during the workshop and afterwards. The discussion room appeared successful in enriching the workshop by providing an opportunity for delegates to find others with similar interests and discuss topics of mutual interest.
One delegate managed not only to contribute to online discussions but also updated his Blog during the event [16]:
"Suffering from typing fatigue - today I've blogged, wikied, IMed and actually talked and listened. Part of the point of today was to look at all these technologies and their use, and I feel like I've given them a pretty good workout."
Two other delegates provided Blog entries after the event. Trafford focussed on the potential of Blogs for use in e-learning [5]. In the UCISA Blog [17] Pope (who was a member of the workshop organising committee) provided comprehensive notes on the presentations, discussion groups and experiences with a variety of technologies. Pope kept a copy of the UCISA Blog entries elsewhere [4] in order to ensure that the information is not lost after her imminent departure from UCISA, providing an example of an issue discussed during the event - the persistency of information managed by Blogs and other technologies. Subsequently the UCIUSA Blog was deleted, providing an valuable illustration of the dangers of loss of digital information and the need for preservation strategies.
In his opening talk Kelly made use of the Skype Internet telephony application [8] to enable a remote user to listen in to the presentation (and engage in discussions using instant messaging technologies). This provides another mechanism for allowing more delegates to have some involvement in events. One minor problem experienced was the changing sound levels as the speakers moved away from the static microphone. If this experiment is to be repeated it will be necessary to provide improved audio capabilities, such as use of a Bluetooth microphone.
The use of computer supported communication (CSC) or computer-supported collaborative work (CSCW) technologies in the seminar environment can be rewarding. However, there are a number of practical and legal preconditions that must be considered.
Practically, the technology required includes a wireless network - or excellent availability of wired machines. The accessibility issue at the time of the event is significant; according to experience, the availability of suitable devices owned by delegates is likely to be low. Given that most such systems have a battery life of between one and four hours, the provision of power supplies is vital; however, solutions must be chosen in light of the applicable legislation e.g. health and safety issues and potential requirements that devices be electrically tested before use.
Wireless network access usually involves set charges from the organisers or hosts, which are generally taken into account during the planning stage. These charges should be revisited following the event in light of experienced network availability. An important precondition to set when choosing a venue is the actual use policy of the network, together with a statement of required network availability and bandwidth, including any potential bandwidth charges.
A further issue requiring attention before the event involves access management; are usernames and passwords necessary to access the network? What security has been implemented on that network, and are all devices likely to support that system? A budget must be set aside for technical support, both for network access issues and for technology use issues. It is to be hoped that in future network access problems will lessen further due to technologies such as the IETF Zeroconf protocol [18], an automatic DNS-over-IP configuration system that attempts to automate the process of joining a network.
Costings for such an event must take these factors into account and there will be a need to define an appropriate costing model (e.g. delegates pay per use, or access included in registration fee). There will also be a need to have contingency plans in case of difficulties accessing the network.
The actions necessary to ensure security are often at odds with usability and accessibility. Wireless networks will generally require several levels of security, potentially including Web or network proxies secured by username and password combinations, MAC address filtering, establishment of SSID (network name) and the proven-insecure WEP (Wireless Encryption Protocol). These details should be established before the event and shared with those individuals responsible for technical support.
Unfortunately, the unexpected can also occur; for example, a conference delegate with a worm- or virus- infected laptop could easily infect a number of other users. Since it is not possible to effectively protect each networked machine from its peers from a network administration perspective, one must consider this as a potential failure point and take steps, perhaps by requiring or strongly advising each user to run a personal firewall such as ZoneAlarm [19] and by requesting that each user consider the installation of a virus checker.
In practice, not all CSCW technologies scale evenly to all scenarios; for example, Wiki pages are 'locked' during edits, so a group of no more than four or five people can be enough to ensure that the Wiki is almost never available for editing. Instant messaging tends to suffer from similar problems of scale, as does IRC (Internet Relay Chat); many people talking on a single chatroom produces a similar scenario to many people talking in a single hall.
Fortunately, there is a solution to this: formalisation. A situation involving a hundred people talking simultaneously can easily be formalised, by overlaying a set of rules or conventions. Two possible models might include a lecture theatre or a meeting; in one, students are generally expected to remain quiet unless asking topical questions, and in the other, participants are expected to follow a rigid set of procedures in order to contribute effectively. Similar formalisations may be introduced in online situations; certain systems, such as IRC, provide mechanisms whereby the participants are restrained from breaking their 'rôles' - for example, if one wished to simulate a lecture theatre, one might choose to remove 'voice mode' - the ability to write to the chatroom - from most of the auditors.
The availability of CSCW technologies provides flexible support for a variety of scenarios, making participation in an event possible over a larger timeframe and removing the necessity to be physically present. There are significant advantages to this, particularly in teaching and learning. In order to gain the most out of these media, it is imperative to use them as part of an integrated strategy; revisiting the same theme over time, discussing that theme, and providing opportunities to gain experience and encouragement are all excellent motivations to make use of such technologies. Information is more easily retained when it can be put to use; application of new skills and knowledge is strongly advisable.
A training period for underlying (prerequisite) technologies must be factored in and if possible scheduled shortly before each event to ensure that users are comfortable with the applications in use throughout the event. Activities may be planned following the event, in order to 'debrief' and to share reactions to the information presented, or to provide opportunities to experiment with the various new skills or enabling technologies mentioned throughout the conference. The choice of activities should ideally be made in order to guide learners and promote data retention through recall.
Use of technology in a new setting may fail for at least some participants. To some extent this is avoidable. It may fail because its uses - or the users' objectives - are not well explained or understood. It may fail because the technology as it is perceived simply does not meet user requirements. The reasons for such failures are often subtle, or at least difficult to predict, but a number of issues to consider before technology deployment are noted below:
Having addressed the issues described above, it will be advisable to develop an Acceptable Use Policy which covers use of networked technologies during an event. The Acceptable Use Policy developed for the UCISA/UKOLN Workshop is available at [12]. However although this may have been appropriate for that particular event, it may not necessarily be applicable in other situations. A framework for developing an appropriate Acceptable use Policy is given below.
Initially there will be a need to address policy issues. Will a networked environment be provided and, if so, what is its purpose? Will this be available in the background, for delegates to use if they so desire or will the event organisations seek to use the infrastructure in a pro-active fashion? How will the provision and support for the infrastructure be funded?
Is it intended to provide recommended applications or leave users to choose for themselves? Recommendations can help to reduce support difficulties. It may be desirable to provide an opportunity for delegates to learn how to use the applications and appreciate how they may be used prior to the event, in order that learning to use the applications does not distract from the event itself.
There will be a need to provide adequate networked security or, if this is not possible, to advise delegates of the importance of security for their networked devices. There will also be a need to address the confidentiality, security and retention of information created during the event.
There will be a need to develop a policy which addresses potential concerns over the possible disruptive or intrusive aspects of use of the technologies. In some settings this may be developed in an ad hoc fashion, but for more formal events there may be a need to ensure that delegates agree to a code of conduct when registering.
There will also be a need to identify responsibilities for ensuring delegates are aware of, and if necessary, enforcing an AUP.
There will be a need to identify a funding model for the provision of the networked infrastructure, the management of usernames and passwords, technical support, etc. In many research conferences, this may be provided in the conference fee, but in commercial venues there may be charges based on usage. There may also be a need to establish service level agreements, and possibly recognise the need for rebates or penalties if an acceptable service is not provided.
The JISC-funded QA Focus project developed a series of online toolkits which were intended to provide a simple interactive form which could be used to ensure that projects were implementing appropriate standards and best practices. This approach has been extended in order to develop a toolkit which can be used by event organisers who are considering providing access to networked applications at an event [15].
The toolkit is based on the issues which have been raised in this paper. The responses provided when answering the questions provided in the toolkit are intended to ensure that relevant issues are addressed. The toolkit is intended to be extensible, with links to examples of case studies and best practices provided.
The toolkit is illustrated in Figure 4.
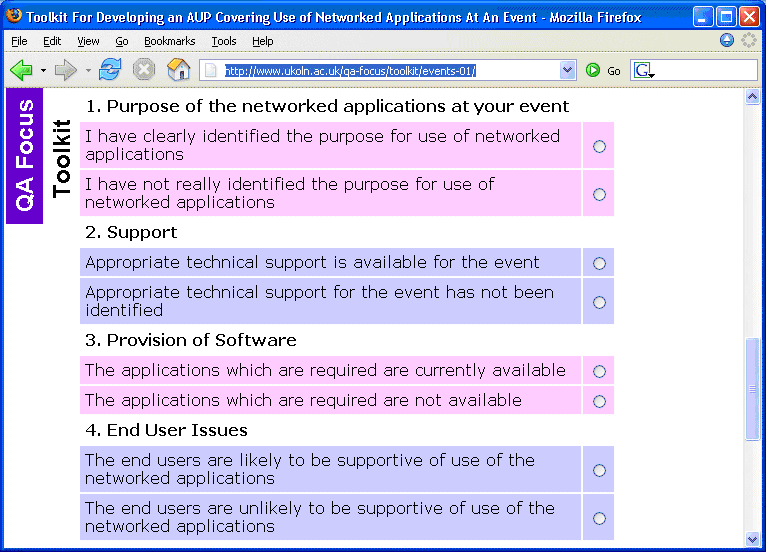
Figure 4: The Online Toolkit
This paper has described the experiences of actively using networked technologies to support a workshop. The potential for enhancing the learning processes in a conference environment have been discussed. The paper highlights some of the potential dangers to be aware of and provides advice on suitable approaches which can be taken and a framework which can be used to develop an appropriate acceptable use policy.
The authors intend to build on this work in further events and welcome the opportunity to share experiences with others involved in related activities.
Using Networked Technologies To Support Conferences, Kelly, B., Tonkin. E. and Shabajee, P. EUNIS 2005 Conference Proceedings (CDROM). <http://www.ukoln.ac.uk/web-focus/papers/eunis-2005/paper-1/>