JISC Head of Programmes
A sound authentication system is recognised to be a fundamental requirement of a distributed electronic resource, and development of a suitable system is a high priority in the UK. This paper describes the JISC’s activities in the authentication field which are following three separate strands:
The JISC operates three data centres and several services in the UK, shown in Figure 1 [95]. These three centres are funded by JISC to provide access to large datasets. They are:
BIDS: Bath Information and Data Services.
EDINA: Edinburgh Information and Data Access.
MIDAS: Manchester information and Datasets and Associated Services.
The JISC is also responsible for thirteen services and projects, shown in Figure 2.
AGOCG: advisory group on computer graphics, a "think tank "funded jointly by the disc and the engineering and Physical Sciences Research Council.
AHDS: The Arts and Humanities Data Service.
BUBL: Formerly the Bulletin Board for Libraries. BUBL Provides subject based access to internet resources and services including a specialist service for the library and information science community.
BUFVC: British Universities Film and Video Council. Funded for the advancement of higher education by the co-ordination and development of the use of film and related media, materials and techniques for the purposes of teaching and research.
CHEST: The Combined Higher Education Software Team negotiates bulk deals on software and electronic information for the higher education community.
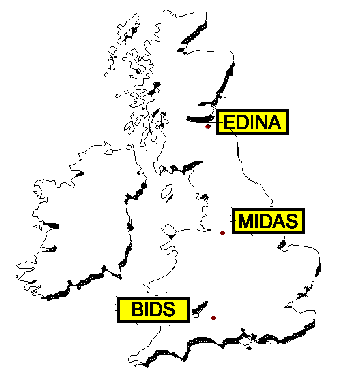
Figure 1: JISC Data Centres
COPAC: A project to provide on line access to the CURL (Consortium of University Research Libraries) library catalogues.
DATA ARCHIVE: A long term repository for social sciences and history datasets.
HENSA: Higher Educational National Software Archives; two services providing shareware (an exchange of free software and information) and caches.
MAILBASE: A JISC funded service offering managed mailing lists for discussion groups and discriminating information.
NETSKILLS: A project to provide training in the effective use of network information resources. It forms part of the eLib programme and is funded by the JISC.
NISS: National Information Service and Systems. A JISC funded service providing access to external electronic information and a bulletin board for the JANET (Joint Academic NETwork) community.
SOSIG: Social Science Information Gateway. Currently jointly funded by the Economic and Social Research Council and JISC as an eLib project.
UKOLN: The UK Office for Library and Information Networking. A national centre for support in network information management in the Library and Information communities. It is jointly funded by the JISC and the British Library.
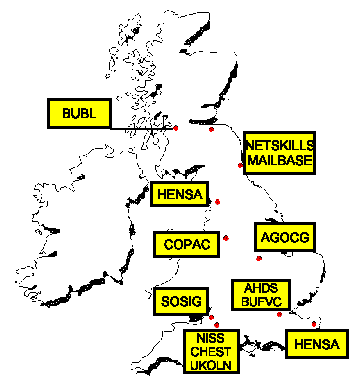
Figure 2 JISC Services and Projects
At present much of the work is concentrated on creating a common interface for the data centres. These provide a wide range of electronic services – bibliographic, socio-economic, scientific and geographical data services and on-line journals to name a few – and have, up to now, adopted separate approaches to authorisation and user naming schemes.
Some of the other services may wish to introduce subscriptions or other controls on access in future, and there are also many projects running across the UK which could develop into services in their own right eventually.
There is, then, a plethora of existing and potential services that require a common authentication system if they are to provide an aggregated total service. Allowing each to develop its own system would be wasteful of effort and would serve to alienate rather than encourage use of these services. We have therefore identified the need for a common authentication service, which has four key requirements.
The first requirement is a common user identification scheme for the three existing data centres; secondly, users will have a single password for all services. Third, the system set up for the data centres will be the model that emerging services can adopt to control access to their data. And finally, any solution must be quick, since it is recognised that it is probably a stop-gap solution; cheap, which rules out a major development programme; and simple to manage, or we risk alienating the intermediaries in information services, who have to administer the system.
The solution adopted is to develop an existing software product which is already in use by over 150 higher education (HE) institutions in the UK. This is the ATHENS system which was developed by our NISS service at Bath. In the longer term the intention is to move to a commercial system.
Details of the ATHENS package can be found on the ATHENS Web pages [96], but it is worth noting a few key features. In essence, ATHENS controls access to Web pages centrally, while allowing local control. The package runs on a central server, not locally. It is based on a leading commercial package, SYBASE, which is used by several banks to control their ATM transactions. Trials indicate that it has adequate capacity to deal with the UK authentication traffic but replication of servers will guarantee reliability and spread the network loading.
A key development feature is to make the administration as simple as possible. An administrator can load and maintain user information locally and download this in bulk to the server when required. User names are largely under the control of the site, and there are facilities for automatic user name generation. There is flexibility for creating group ids, and local delegation of authority for granting access, with control over how access rights are delegated. This can spread the administrative load across the campus. Support and training for administrative staff is also planned, which it is vital for gaining acceptance of the new system.
The advantages the user will see are single user names and passwords for access to all JISC services, user profile facilities to store preferences and status of previous searches, and reasonable privacy. The system was not designed to guarantee privacy but offers some protection:
Reliability and resilience are achieved by deploying multiple servers; the system features automatic, reliable replication. The service will also be available to sites to control access to their local data on the Web. For example confidential or sensitive data can be protected and access to local content, for example lecture notes or teaching material, can be restricted to local users. This feature will also provide a common control mechanism for local and remote electronic services – the user ideally should not be aware of the difference.
Another benefit which the service will bring is confidence on the part of content suppliers that HE can properly manage and control access to their products so their rights will be protected. As a side effect, we will be able to move away from the use of IP address checking. JISC is also encouraging services to become self funding; limiting access to subscribers can help guarantee revenue streams.
Timescales for this work are quite short; we view the plan as aggressive, but realistic. Coding is advanced and is on target for completion by the end of June 1997. Testing with the three data centres will then begin and the service will be ready by the start of the 1997/98 academic year. The data centres will migrate their services onto the new system at different rates. One already uses it, albeit with group id’s only; one intends to move all its services as soon as possible; and one plans to migrate some services now, and the rest later. It will be available generally for other services and for local use from January 1998.
The JISC recognises that ATHENS can, at best, satisfy only a small part of the total requirement, since the volume of traffic across the network to access national services is a fraction of the internal network traffic within an institution. A solution is needed for secure intra-institute traffic but there is a wide divergence of views about the form this should take. At one extreme, some sites believe only strong authentication and full encryption services will satisfy the need; at the other some sites believe it must be kept very simple, if not avoided altogether. The JISC has identified a range of services which might require authentication, and investigated the technologies available to achieve these.
It is important though not to introduce electronic solutions which exceed the security provided by existing procedures. Encrypting documents which are then printed and left lying on desktops is an expensive waste of effort. Currently JISC is conducting a survey to establish what the real business needs of HE are for these services This will identify what form solutions will take, though the divergence of institutional operations means a common approach is unlikely to be found. However, once the needs are established it will be possible to identify areas where more information is needed, pilot systems to investigate these and document best practice. It is planned to set up a smartcard demonstration facility at Aston University.
For the present JISC’s data services are free at point of use, so there is no imperative to find a solution for commercial activities on the network. It is not difficult to see that the demand for these will not be far off. The JISC anticipates forming a partnership with one or more commercial partners who can bring a "business infrastructure" to provide strong authentication, charging, billing and non-repudiation services. This will complement HE’s data ownership, navigational and management strengths. This can offer a solution for data and service suppliers who do not already have their own systems in place or want to be compatible with HE . It will more importantly allow UK HE to sell its services and data to outside bodies, possibly co-operatively, without having to develop or manage their own commercial infrastructure if they do not wish to. This is an area where there is a strong case for international collaboration.
[94] This account was prepared for this report by The Marc Fresko Consultancy. It is based on text adapted from a paper supplied by the speaker and slides used during the presentation.
[95] The maps in this paper are based on originals from the Manchester City College Web site.